The 9-Minute Rule for Risk Management Enterprise
Not known Incorrect Statements About Risk Management Enterprise
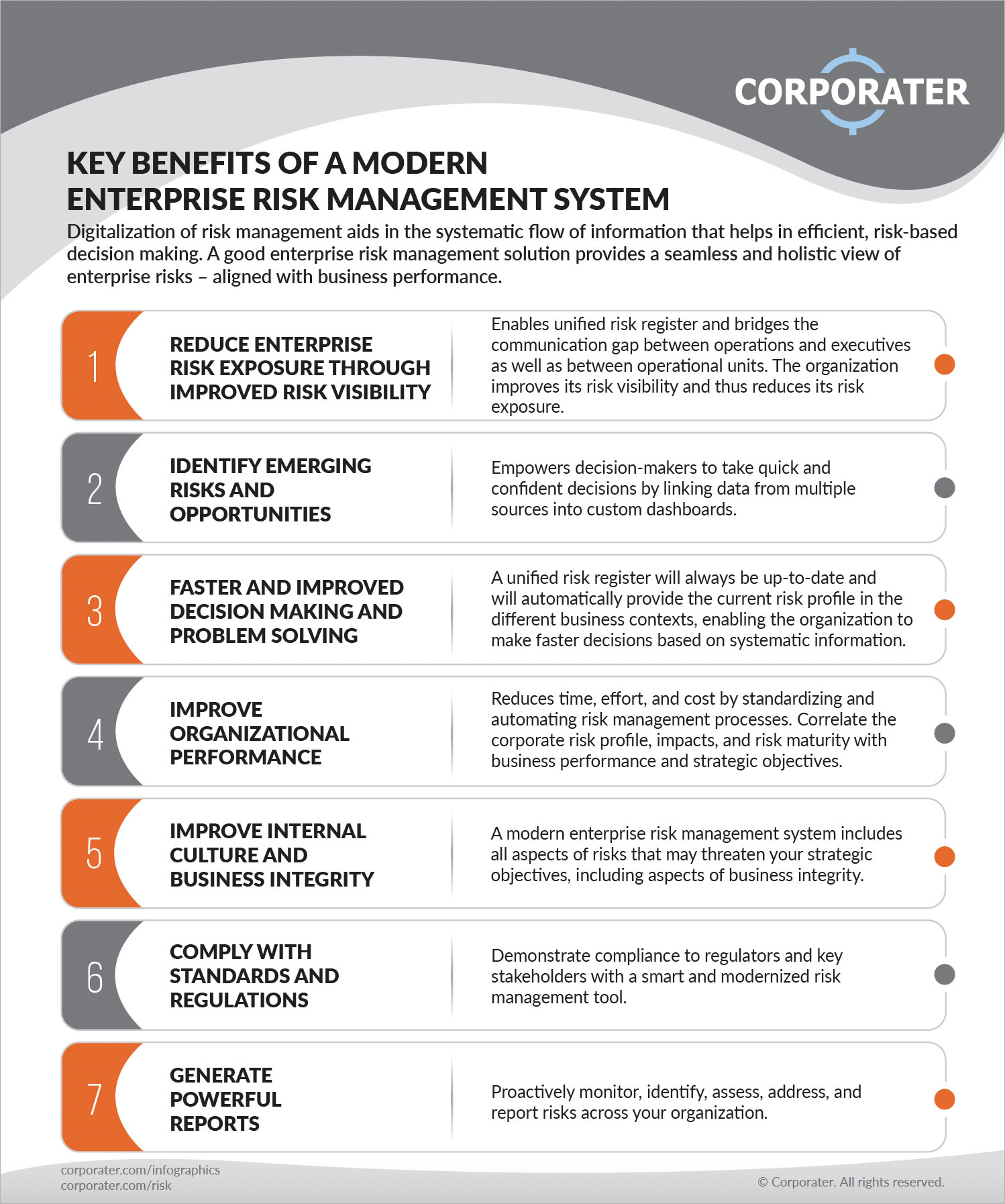
Table of ContentsAll About Risk Management EnterpriseThe Basic Principles Of Risk Management Enterprise Facts About Risk Management Enterprise Revealed
Control who can see or modify these elements by setting certain access legal rights for private users, making sure info safety and customized use. Enables users to tailor their user interface by choosing and arranging important data elements. Offers a tailored experience by allowing personalization of where and just how information components are shown.It allows accessibility to real-time integrated data instantly. Facilities can utilize comprehensive data intelligence for quicker and a lot more informed decision-making.


Diligent is a risk monitoring software application that permits maximizing performance, and enhances development. It likewise aids monitor dangers with ERM software that consists of integrated analytics and adapts to your service needs. This software comes with numerous valuable functions. Below we have highlighted one of the most essential ones. So, examine them out.
Top Guidelines Of Risk Management Enterprise
Simplifies the process of gathering risk information from numerous parts of the organization. Offers management and the board with real-time threat insights. Usage ACL's sophisticated analytics to spot threat patterns and forecast risks.
This permits firms to record risk insights website and red flags in the third-party vendor's security report. Enables companies to catch and document danger insights and red flags in third-party supplier protection reports.
It additionally reduces danger with structured conformity and risk management. It can help gather and track all your dangers in the Hyperproof threat register.
It supplies fast accessibility to needed info and paperwork. This makes sure the protection of Active proof instances by allowing multi-factor authentication (MFA) making use of authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
The 6-Minute Rule for Risk Management Enterprise
It supplies top-tier protection functions to guard sensitive data. This threat administration software program is an ideal tool for centers looking to fix unneeded issues or threats.
Users can likewise utilize the AI-powered tools and pre-existing web content to create, examine, focus on, and address dangers efficiently. Enhances the procedure of configuring and occupying risk signs up. Utilizes AI and library web content to improve danger evaluation precision. It enables quicker identification and mitigation of risks, This is generally an aesthetic version.